

Real-Time Threat Detection with Autonomous Learning Model examines how AI-powered systems can identify and respond to cyber threats, leveraging autonomous learning models to enhance their capabilities. This minimizes damage and response time. It covers the use of algorithms to detect anomalies, intrusions, and malware in real-time data flows. The blog highlights the system architecture, key paradigms, and practical challenges such as delays and false positives. It also discusses real-world tools and evaluation metrics. This approach makes cybersecurity solutions more intelligent, faster, and adaptable to the modern digital environment.
Real-time threat detection is the process of identifying cyberattacks or suspicious activities. Just as they are not after the loss. Traditional security systems register or analyze alerts after an incident. Which may be too late. Real-time systems use tools and techniques to continuously monitor the behavior of networks, users, or devices. When an unusual or harmful thing is detected, such as a sudden increase in data traffic or the start of a session from a strange place, an alert is immediately generated or action is taken. This helps to prevent risks before they cause damage, such as stopping a hacker or isolating an infected system. Real-time detection is essential to protect sensitive data, financial systems, and critical infrastructure. It is based on automation, high-speed processing, and maximum automated/ machine learning models to identify new and emerging threats. It's like a security guard who sees everything 24/7 and reacts immediately before danger. The faster the reaction and the less damage it will cause.
Traditional security systems rely on fixed principles. Such as "block IP if it tries to log in 5 times," but attackers easily bypass them in new ways. Machine learning (ML) goes beyond the rules by learning patterns in the data (such as login behavior, traffic flow, or file activity) and detecting abnormal activity on its own. It can detect unknown or zero-day threats that do not match an existing signature. ML models such as Random Forest, SVM, or neural networks describe behaviors as normal or suspicious using statistical models. Unlike static rules, ML aligns over time, making it difficult for attackers to remain hidden. It also handles large amounts of data in real-time, where manual analysis is impossible. With the right training data, ML can reduce false alarms and respond to real threats faster. In short, ML adds intelligence and flexibility to threat detection, helping both humans and systems stay ahead of cyber attackers.
Machine learning can detect a wide range of cyber threats by analyzing patterns in system and network data.
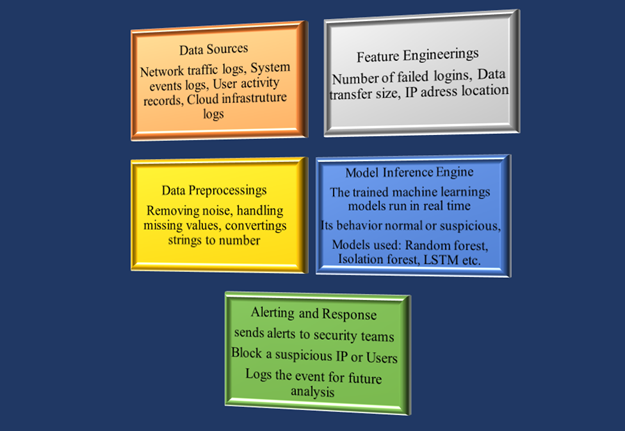
The real-time ML-based threat detection system is built like a pipeline that collects, processes, and analyzes data continuously. It starts with collecting data from sources such as logs, network traffic, system events, or cloud services. This is followed by data preprocessing and feature extraction, where useful indicators, such as IP address, login frequency, or file size, are converted into numeric attributes. These features are sent to a machine learning inference engine that uses trained models (such as a random forest or neural network) to detect suspicious patterns. If there is a risk so the alerting module triggers responses such as blocking IP or notifying security teams. For streaming data, tools such as Apache Kafka and Spark Streaming are used to maintain speed and scalability. All components must work with low latency. So that the risks are caught immediately, not minutes later. This architecture ensures continuous learning, fast decisions, and effective responses to changing cyberattacks.
Different ML models are used in risk detection based on the type of data and the problem to be solved. Deciduous trees and random forests are famous for their simplicity and accuracy in classifying known patterns of invasion. Logistic regression is currently used. When interpretation is necessary perfect for binary decisions such as safe vs. doubtful. To detect rare or hidden threats, isolated forests and one-class SVMs help in the identification of anomalies. In more modern systems, neural networks are used for complex behavior, and LSTM (long short-term memory) networks are particularly good at handling logged activity in a time-based setting, such as hours or days. Auto encoders are useful for unmonitored anomaly detection by learning general behavior and a compact representation of flagging deviations. The choice of model depends on the use case, available data, and the need for speed versus accuracy. These models are trained on past behavior and deployed in real-time pipelines to detect threats.
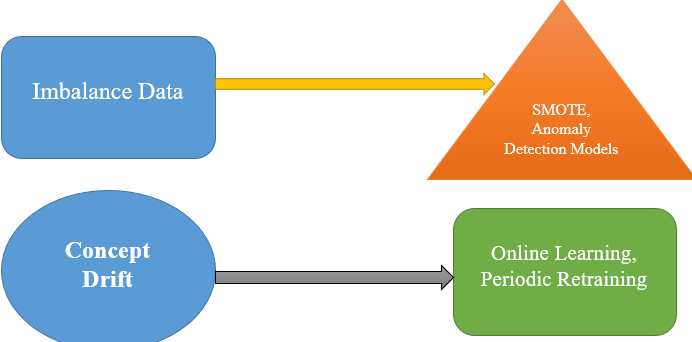
Real-time ML systems face many technical challenges. A major problem is unbalanced data, where most records are stored, and there are only a few risks - this can make models biased. Techniques such as SMOTE (Synthetic Minority Over-sampling) or anomaly detection models help to fix this. Another problem is the concept of escalation, where the attacker's behavior changes over time. To address this, models must be regularly retrained or use online learning that is updated in real-time. The delay is also important. Models should make rapid predictions (in milliseconds) to prevent immediate hazards. Too many false positives (false warnings) can overwhelm teams, while false negatives (reduced risks) are dangerous. A balance of accuracy and memory is required. Scaling the system to handle high data volumes (such as in enterprise networks) also requires efficient infrastructure such as Kafka and Spark. Solving these challenges ensures accurate, rapid, and adaptive risk identification.
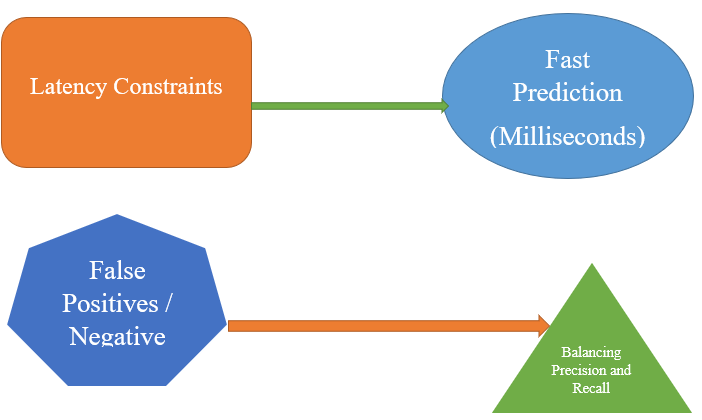
To find out if the risk detection model is working well, we use diagnostic metrics. The most basic is accuracy, but in cybersecurity, it can be misleading due to unbalanced data. That's why we used Precision (how many predicted risks were risks) and Recall (how many real risks the model captured). A good model should have more memory to avoid missed attacks and more accuracy to reduce false alerts. F1 - Balances both scores, giving the same score. For probabilistic models, ROC-AUC (Receiver Operating Characteristic-Area under Curve) shows how well the model distinguishes threats from protected events. In real-time systems, we also take care of delays (how fast the model predicts) and throughput (how much data it can handle per second). These metrics guide improvements to the model and help teams trust the detection system.
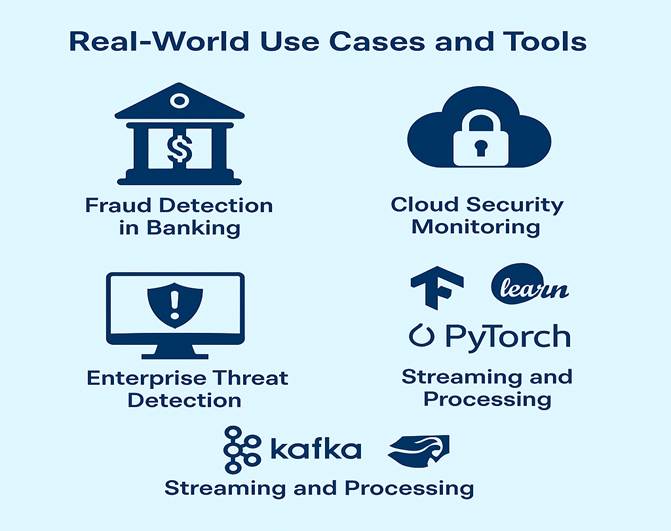
Real-time ML-based threat detection is widely used in modern cybersecurity environments. Banks and financial institutions use it to catch fraud and unusual transactions instantly. Cloud providers such as AWS and Azure integrate ML to detect unauthorized access or data leaks. Enterprises use it in their SOCs (Security Operations Centers) to monitor user behavior and prevent insider threats. Tools such as Splunk, Elastic Stack (ELK), and IBM Q Radar integrate ML for advanced analytics. For custom ML, platforms such as Tensor Flow, Scikit learn, and Py Torch are commonly used. Streaming and real-time processing are powered by Apache Kafka, Apache Flink, or Spark Streaming. These systems often combine with firewalls, anti-virus, and SIEM solutions to form a layered defense strategy. In short, detecting ML in real time is not just theory. It's actively protecting real businesses and governments every second.
Machine learning has transformed real-time threat detection by enabling systems to respond faster and smarter than ever before. From anomaly detection to zero-day threat detection, ML helps reduce damage and automate defense. However, challenges such as evolving attacker behavior, data asymmetry, and system latency still require continuous improvement. In the future, self-learning AI systems, federated learning, and explainable AI (XAI) will play a big role. Models will be able to learn from global data securely and offer more transparency. Integrating ML with edge computing and IOT security will extend its use beyond traditional networks. Cybersecurity is a fast-moving field, and ML-based detection will continue to evolve to address more complex, fast-moving threats. To stay ahead in this digital arms race, organizations must invest in skilled teams, robust data infrastructure, and adaptable ML systems.
Powered by Froala Editor