SIEM is a technology that collects security-related data from the entire IT system, such as from servers, firewalls, and applications. You will analyze the data. It says that there is no hacker attack. The SIEM system sees in real-time what's unusual happening and sends an alert when there is a risk. Such companies can prevent cyber Attacks and also comply with the law. (HIPAA, or PCI-DSS). Machine learning is also used in SIEM nowadays to smartly detect the most dangerous threats. SIEM is the star of an intelligent security guard who keeps an eye on every place.
Introduction
SIEM (Security Information and Event Management) is a software system that helps organizations monitor their IT environments for security threats. It does this by collecting logs and security event data from various devices such as firewalls, servers, operating systems, antivirus tools, and applications. After the data is collected, SIEM tools analyze and correlate the information to detect suspicious behavior such as failed logins, abnormal transfer of data, or malware activity. SIEM acts as a central brain for cybersecurity teams, providing them with real-time alerts, visual dashboards, and detailed reports to take immediate action. It is particularly useful for early risk detection, compliance reporting (e.g., GDPR, HIPAA), and forensic investigations. Modern SIEMs also use machine learning and behavioral analytics to improve detection accuracy. Whether you're a beginner learning how logs work or an expert tuning detection rules, SIEM offers a unified, intelligent way to secure digital infrastructure.
Core component of SIEM Systems
A SIEM system consists of several components that work together to detect threats and manage security data.
- Log Collection. In this step, SIEM gathers logs from different sources such as firewalls, servers, operating systems, antivirus, and applications.
- Normalization: Raw logs have come in different formats. SIEM standardized this data so it can be analyzed uniformly.
- Correlation Engine is the heart of SIEM. It links related events, e.g,. Multiple failed logins and data downloads identified a suspicious pattern.
- Alerting System when something unusual is detected, SIEM generates alerts, thus the security team can take sudden action on it.
- Dashboard and Reporting gave a visual overview of system health, detected threats, and compliance status by using charts and graphs.
- Forensic and Historical Analysis, in this SIEM, allows you to go back in time and investigate how a security incident occurred.
How SIEM Works
- Data Sources such as firewalls, routers, servers, applications, and endpoints continuously generate logs and security events.
- These logs are collected and sent to the SIEM system using protocols like Syslog, SNMP, or API integrations.
- SIEM performs normalization and parsing, converting different log formats into a common readable structure.
- The correlation engine then analyses relationships between events, e.g., repeated failed logins and file access is a possible brute-force attack.
- If a threat pattern is found, the system generates real-time alerts based on predefined rules or behavioral anomalies.
- These alerts are shown on dashboards with severity levels, timelines, and affected systems.
- Security teams then use this information for incident response, threat investigation, or automated action using SOAR tools.
- This structured flow enables SIEM to act as a real-time decision-making hub for security operations.
Diagram
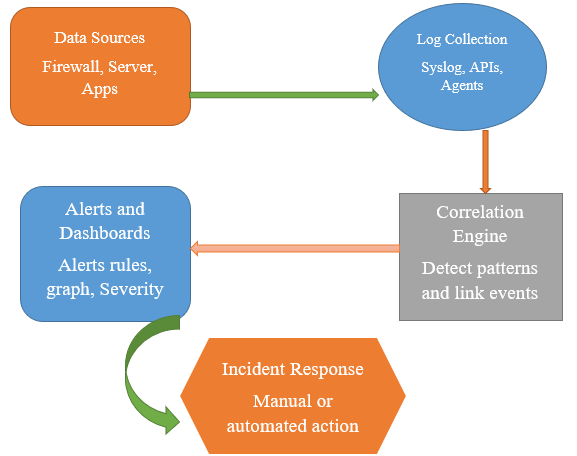
SIEM Use Case from Compliance to Threat Detection
SIEM systems are used in many ways to improve an organization’s cybersecurity and meet legal requirements which need.
- Threat Detection: SIEM identifies suspicious activity, like brute-force logins, malware behavior, or insider threats, by analyzing event patterns.
- Incident Response: When a threat is detected, SIEM provides detailed alerts and timelines, helping the security team act faster.
- Regulatory Compliance: SIEM helps meet standards like PCI-DSS, HIPAA, and GDPR by storing logs securely and generating automated compliance reports.
- User Behavior Analytics (UBA): Advanced SIEMs can learn normal behavior and flag unusual actions, like logging in from a new country.
- Forensics & Investigation: SIEM logs allow deep historical analysis to trace how an attack happened and what was affected.
- Operational Visibility: Dashboards give insights into system health, login trends, and access anomalies, supporting daily security monitoring.
- For experienced people, SIEMs offer custom rule writing, integration with threat intelligence, and machine learning for smarter detections.
Role of Machine Learning in Modern SIEM
Traditional SIEMs rely on static principles, which often produce a lot of false positives or miss out on unknown risks. Modern SIEMs now use Machine Learning (ML) to make threat detection more intelligent and adaptive.ML models can learn from historical log data to understand what is "normal" and flag anomalies such as abnormal login times or abnormal data transfers. Techniques such as clustering, classification, and unsupervised learning help detect complex threats that static rules cannot capture. For example, User and Entity Behavior Analytics (UEBA) uses ML to monitor each user's behavior and raise alerts when it changes suddenly. These models reduce alert fatigue to improve the accuracy, and alerts can also be prioritized based on risk. Advanced users can train custom ML models or existing models using data pipelines and feedback loops. This integration of ML transforms SIEM from a rule-based system to a predictive, adaptive risk-taking platform.
Diagram
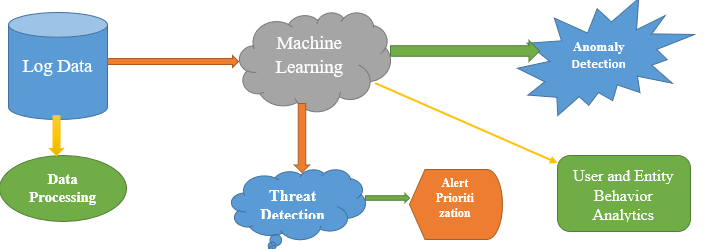
Challenges in SIEM Implementation and Management
SIEM provides powerful security capabilities, which are implemented on it is not easy.
- High Volume Data: It collects logs from all systems that can produce a terabyte of data daily, which creates storage and processing challenges.
- False Positive; It weakly tuned rules, which may generate too many unnecessary alerts, over security teams' alert fatigue.
- Complex Setup: This SIEM integration requires a deep understanding of the network architecture, log formats, and custom use cases.
- Skilled Resources required; this organization needs to train analysts to write correlation rules, interpret the dashboard, and fine-tune alerts.
- Cost and Licensing: Enterprise-grade SIEM tools can be cheap, especially with growing log volumes and retention requirements.
- Log Quality Consistency; in this which logs that are incomplete or inconsistent can cause blind spots in threat detection.
Those who are more expert often use automation, SOAR tools, and Threat Intelligence feeds to reduce manual effort and improve its efficiency.
SIEM vs SOAR
- SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both used in security operations, but they play different roles.
- SIEM focuses on collecting, analyzing, and linking security data to detect threats and generate alerts. It helps in visibility, compliance, and risk detection.
- SOAR, on the other hand, is designed to automate response operations such as disassembling a device, sending alerts, or initiating an investigation.
- Once SIEM identifies a threat, think of SIEM as the "brain" that detects problems
- SOAR is the "hands" that take action.
- SOAR platforms are also integrated with ticketing tools, playbooks, and threat intel feeds to respond to the event.
- Experts often use SIEM and SOAR together to create a faster, smarter, and more automated Security Operations Centre (SOC).
- SIEM helps you to see and understand
- SOAR that helps you to decide and act often in seconds.
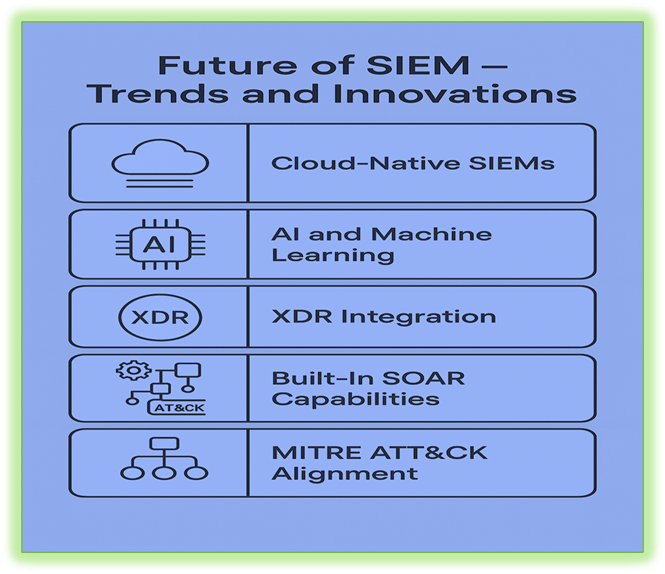
Future of SIEM Trends and Innovation
- SIEM is rapidly evolving to meet the demands of modern, cloud-first, and AI-powered environments.
- A major trend is the addition of cloud-native SIEMs, which offer improved scalability, cost efficiency, and integration with cloud services such as AWS, Azure, and GCP.
- Another innovation is the deep integration of AI and machine learning to enable predictive analytics and detect unknown or zero-day risks.
- XDR (Extended Detection and Response) is also impacting SIEM by combining endpoint, network, and email threat data into one unified platform.
- SIEMs are now embedding SOAR capabilities for built-in response automation, reducing the need for separate tools.
- Support for the MITRE ATT & CK framework is becoming standard, allowing for better mapping of attack behaviors and threat strategies.
- For experts, future SIEMs will allow for customized ML model integration, real-time streaming analytics, and automated threat hunting.
- In short, the future of SIEM lies in automation, AI, cloud integration, and adaptive security intelligence.
Diagram
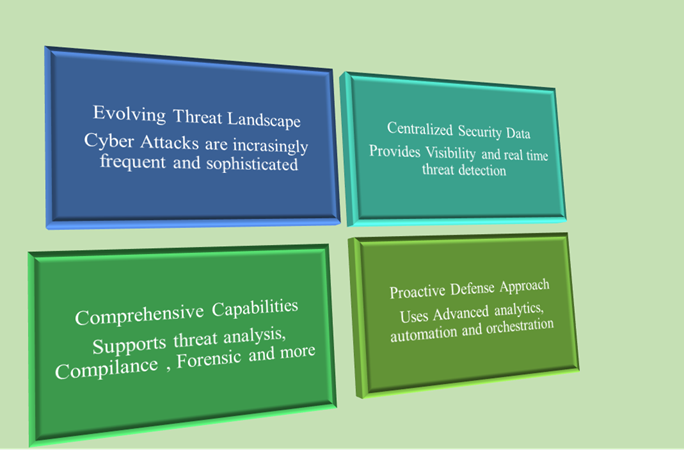
Conclusion
In today's threat landscape, cyberattacks are more frequent, complex, and fast-moving. SIEM plays an important role by centralizing security data, analyzing it in real-time, and helping teams effectively respond to threats.
- For starters, what's happening in SIEM networks and systems provides visibility.
- For experts, it provides deep analytics, customizable rulemaking, machine learning, and integration with SOAR and Threat Intel tools.
- Its ability to support compliance, auditing, and forensics makes it a must-have in all industries.
- With the rise of the cloud, remote work, and IOT, SIEM now helps secure hybrid and distributed environments as well.
- Advanced SIEMs also enable proactive defense by using behavioral analytics, anomaly detection, and automation.
- In short, SIEM is no longer optional; it is a core pillar of modern cybersecurity operations for organizations of all sizes.
Diagram
Powered by Froala Editor





